Enabling Authentication
- Requires PKI (Public Key Infrastructure) or SAP NetWeaver SSO
- If the HTTPS request is terminated by a reverse proxy (SAP Web Dispatcher), the proxy and gateway should implement certificate forwarding in the HTTP header
- Secure credentials caching is needed
- The application should support the change of initial and expired user password
- A password could be locked out as a result of a DDoS attack
- Leverage an external authentication provider (such as SAP NetWeaver Portal)
- Gateway trusts SAP logon tickets issued by the portal based on user credentials
- Requires SAP NetWeaver SSO
- Works only in intranet scenarios
- Requires an additional system – an Identity Provider (IdP) – such as SAP NetWeaver SSO or MS ADFS
- OAuth offers constrained authorization and Single Sign-On for OData Services
SAPUI5 Consumption Architecture
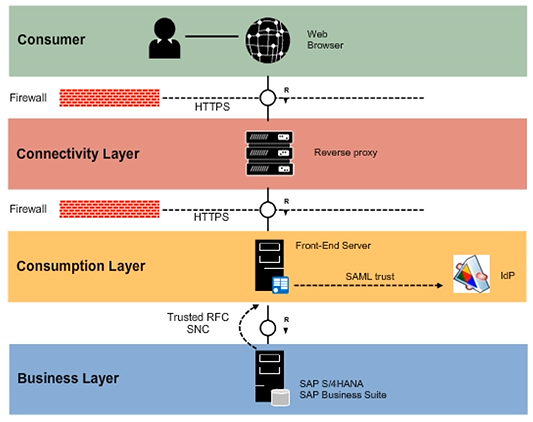
In the figure, the consumer is any client-side SAPUI5 application. This can also be a SAPUI5 application called via a mobile device.
The SAPUI5 consumer application communicates to the customer’s environment via reverse proxy. The reverse proxy acts as a server-side proxy used for avoiding same-origin policy restrictions. The SAP Gateway server also acts as the front-end server for SAP-Fiori-like applications and hosts the SAPUI5 as a business server page (BSP).
Both the SAP Gateway hub and IdP support SAML 2.0 SSO profile with artifact redirect binding. The gateway trusts SAML assertions signed by the IdP certificate.
The SAP Gateway hub uses Trusted RFC Connection to access the SAP Business Suite back-end system with a named user.
Desktop Application Consumption Architecture
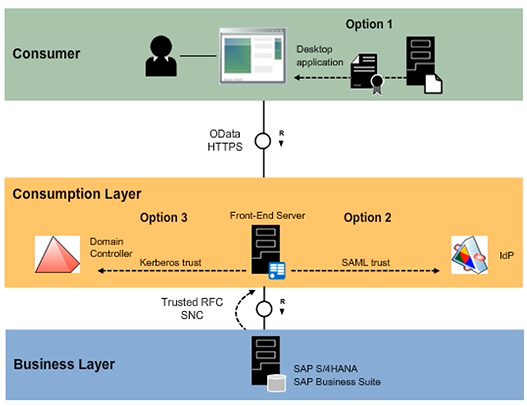
In the figure, the consumer is any desktop application that directly communicates with the Gateway system. One of the following options is used for gateway authentication:
- 509 client certificates distributed using SAP Single Sign-On or PKI
- SAML assertions issued by IdP
- SPNego tokens issued by the domain controller
- User credentials
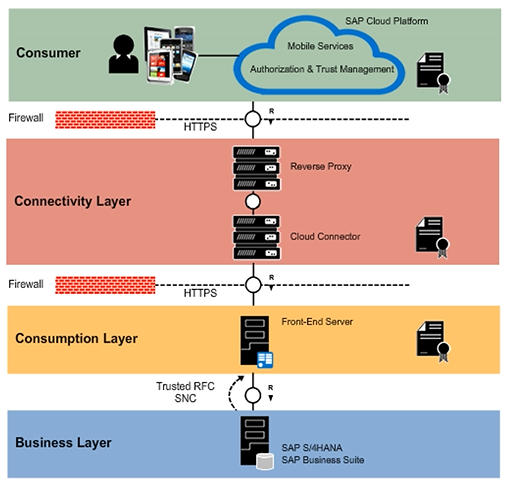
Mobile Application Consumption Architecture
An essential element when planning your SAP Cloud Mobile Services landscape is to provide secure propagation of mobile users' identities to back-end systems. SAP Cloud Platform Mobile Services supports a range of popular application authentication protocols and maps them to back-end systems.
You can use principal propagation that uses SAP Cloud Platform Cloud Connector, which can dynamically transform a user’s identity to a short-lived X.509 user certificate. SAP Gateway supports principal propagation via Cloud Connector. The configuration is required in Cloud Connector as well as the SAP Gateway server to establish trust between the two for principal propagation to happen.
- The SAP Gateway hub has to be configured for SSO based on X.509 certificates.
- The SAP Gateway hub uses Trusted RFC Connection to access the SAP back-end systems with the named user.
Authentication Options for SAP Gateway
The recommended authentication options for SAP Gateway depend on the scenario and consumer.
Authentication Options for SAP Gateway
|
Consumer |
Authentication Option |
|
SAPUI5 applications |
SAML 2.0 Browser Protocol (Extranet) Kerberos (Intranet) |
|
Desktop application (.NET/Java) |
SAML 2.0 Browser Protocol (Extranet) Kerberos (Intranet) |
|
Mobile application (SAP Cloud Platform Mobile Services) |
X.509 certificates |
|
Mobile application (not on top of SAP CP Mobile Services) |