Using Special Techniques with Internal Tables
Binary Search for Standard Tables
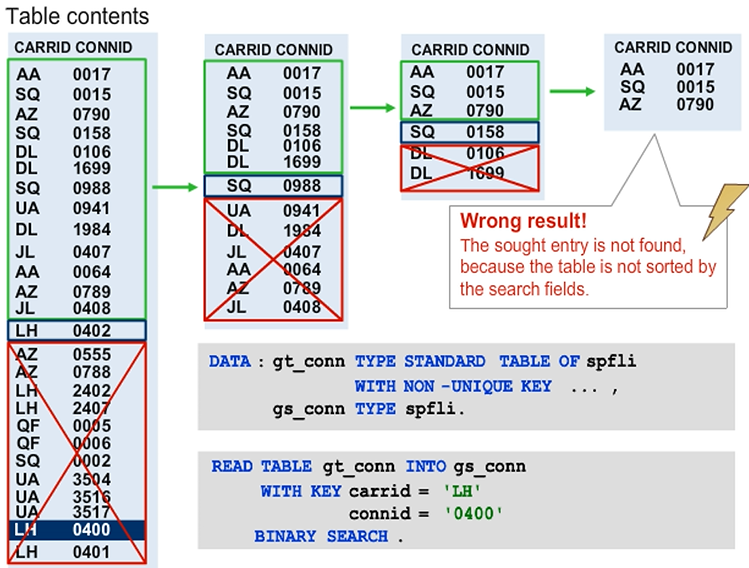
When sorted tables are accessed using their keys, the runtime environment performs a binary search to reduce the access time for large tables. With the BINARY SEARCH addition, you can make the runtime environment apply the same binary search algorithm in a key access to a standard table. Using the binary search during key access is helpful when the internal table is already sorted by the fields you use to restrict access. However, as shown in figure, using a binary search when the table is not sorted leads to incorrect results.
In the example, the runtime environment performs a binary search on the table that is not sorted. After the first step, the algorithm continues the search in the first half of the table because it expects flight LH 0400 before LH 0402. But, because the table is not sorted, the sought entry lies in the second half of the table and is therefore not found.
When using the BINARY SEARCH addition for key access to standard tables, the table must be sorted by the fields used to restrict access. Otherwise, entries may not be found, even though they are contained in the table.
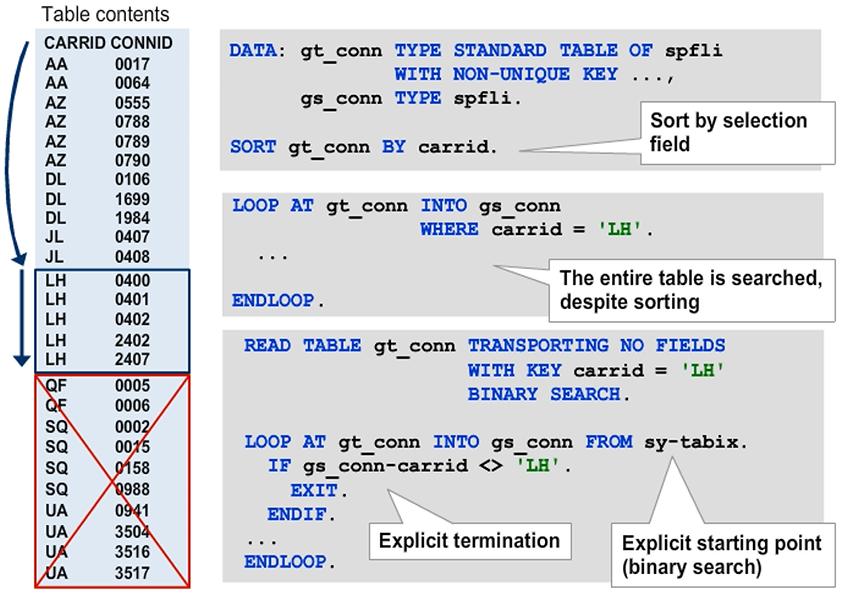
When optimizing performance, you must take into account the additional costs for sorting the table. This extra preparation time is beneficial only if several key accesses are performed with binary search.
Hint: You cannot optimize a single access with the BINARY SEARCH addition if you must sort the table specifically for that access.
Improving Performance of a LOOP using BINARY SEARCH
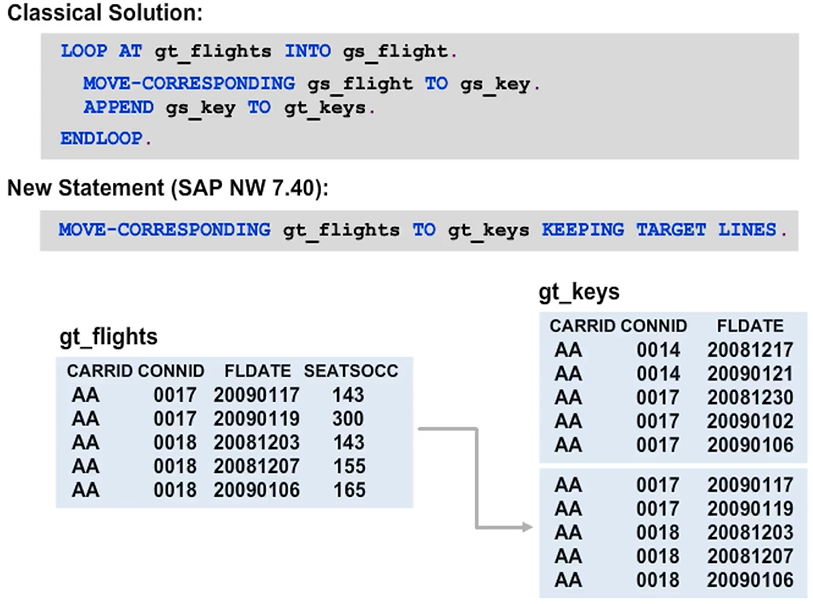
MOVE-CORRESPONDING with KEEPING TARGET LINES Addition
Subtotals During Insert (COLLECT)
The COLLECT statement is a special technique for filling an internal table. The runtime environment aggregates the table already during the insert operation.
If the table does not have a line with the same key yet, the COLLECT statement has the same effect as an INSERT by key. If the table already contains one or more lines with this key, the runtime environment sums the values of all non-key fields in the new line to the corresponding values in the top line.
Hint: The COLLECT statement is only allowed when all non-key fields are numeric. The syntax check reports an error when this prerequisite is not met.
The simplest way to ensure that all non-key fields are numeric is to define an internal table with a standard key (the WITH DEFAULT KEY addition). The standard key is defined such that all non-numeric fields are key fields and all non-key fields have a numeric type.


The figure illustrates how you can use the COLLECT statement to aggregate an existing internal table; that is, create subtotals by group.
The COLLECT statement is a key access, which means you can use it for all three table types.
Caution: Using the COLLECT statement with standard tables can result in poor performance. Keep in mind that the runtime environment has to search for a line with a given key during each execution of COLLECT. With a standard table, this search will take longer and longer the larger the table gets. We recommend that you use the COLLECT statement only for sorted or hashed tables. It is best suited for hashed tables.
Definition of Secondary Keys

Access to Secondary Keys

Update of Secondary Keys
